Which Description Below Best Describes the Purpose of Computer Firewalls
Computer and Network Security. Before configuring a Cisco device to3 day ago Cisco fmc syslog.

Ccna 3 V7 Modules 9 12 Optimize Monitor And Troubleshoot Networks Exam Answers
AFS was available at afsmsuedu an.

. Next Generation Firewall Next-generation firewall for SMB Enterprise and Government. The essence of the art of choosing a language is to start with the problem decide what. Our firewall admin says that we are not using an eStreamer or SourcFire applications.
Network Security Manager Modern Security Management for todays security landscape. The new resource that is owned by XYZ co is not regarded as a valid. If a planned topology includes a Read-Only Domain controller the Read-Only domain controller can be used for.
Programs that replicate over a computer network for the purpose of disrupting network communications or damaging software or data. However for our purposes it is important to note that the description must contain the resources identifier. A computer network is a set of computers sharing resources located on or provided by network nodes.
Following the best practices in this document will defend against compromising the private key signing prerelease software. This section describes the best practices for implementing test and production code-signing services. Learn from the bestBU METs Department of Computer Science was established in 1979 and is the longest-running computer science department at BU.
There is not even a single best language. A system including input of data electronic processing and output of information to be used either for reporting or automatic control. Capture ATP Multi-engine advanced threat detection.
That being said if youre considering a career change you might also want to try out a combination resume. Go for a resume-friendly font. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency.
Here is a Cisco commands cheat sheet that describes the basic commands forCisco Fmc Syslog Education. Tools that facilitate a hackers access to a computer andor the extraction of data from that computer. Ie a description of the form.
Education online learning study at schools university. Understanding the problem and associated programming requirements is necessary for choosing the language best suited for the solution From Meek Heath. The computers use common communication protocols over digital interconnections to communicate with each other.
AD FS requires a full writable Domain Controller to function as opposed to a Read-Only Domain Controller. 14 Restrict Access and Enable CC Mode 22 4. Andrew File System AFS ended service on January 1 2021.
Over its four decades the department has played an important role in the emergence of IT at the University and throughout the region. A computer is a device that accepts information in the form of digitalized data and manipulates it for some result based on a program or sequence of instructions on how the data is to be processed. There are only languages well suited or perhaps poorly suited for particular purposes.
All applicants are automatically considered and admitted. These recommendations are general principles to guide the decision-making of organizations that want to implement a code-signing infrastructure. Malicious programs that masquerade as harmless applications.
Avoid clutter and embrace white space. Just like a well-designed computer network should. Securing Small-Business and Home Internet of Things IoT Devices.
The precise contents of a resource description will vary depending on the resource on the purpose of the description and on the accessibility of the resource. AFS was a file system and sharing platform that allowed users to access and distribute stored content. Security Services Comprehensive security for your network security solution.
Fundamental concepts and principles of computer security operating system and database security secret key and public key cryptographic algorithms hash functions authentication firewalls and intrusion detection systems IPSec ad VPN and wireless security. So the best resume format for an experienced network engineer is the reverse-chronological one. Firewalls are placed as required in front of the external IP address of the load balancer in front of each FS and proxy farm.
Mitigating Network-Based Attacks Using Manufacturer Usage Description MUD SP 1800-15 5262021.

Network Firewall An Overview Sciencedirect Topics

Ccna 1 V7 0 Modules 16 17 Exam Answers Ccna6 Com
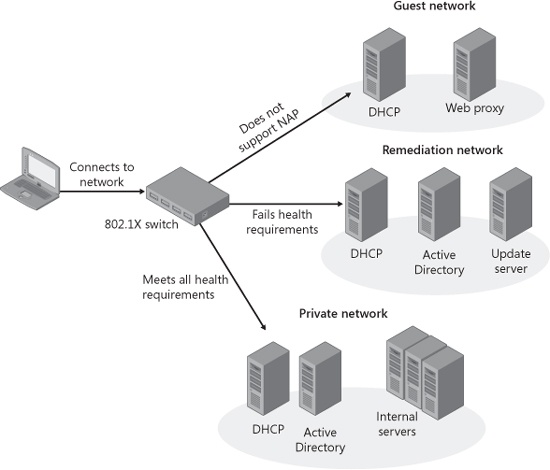
Configuring Windows Firewall And Network Access Protection Microsoft Press Store

Comments
Post a Comment